Monday, December 27, 2010
30. Secure Sockets Layer
Secure Sockets Layer- Cryptographic protocols that provide security for communications over networks like the internet.
27. Copyright
Copyright- The set of exclusive rights given to the author or creator of an original work, including the right to copy, distribute and adapt the work.
24. Wiki
Wiki- A website that lets the easy creation and editing of any number of interlinked web pages via a web browser using a simplified markup language or a WYSIWYG text editor.
23. webapp
webapp- an application that is accessed by a web browser over a network such as the Internet or an intranet.
22. Website
Website- A computer connected to the internet that maintains a series of web pages on the World Wide Web.
21. Web Cache
Web Cache- The caching of web documents e.x., HTML pages, images to limit bandwidth usage, server load, and perceived lag.
20. Web 2.0
Web 2.0- Is usually associated with web applications that facilitate interactive information sharing, interoperability, user-centered design, and collaboration on the World Wide Web.
17. Really Simple Syndication(RSS)
Really Simple Syndication(RSS)- A family of web feed formats used to publish frequently updated works—such as blog entries, news headlines, audio, and video—in a standardized format.
13. Internet Service Provider (ISP)
Internet Service Provider (ISP)- A company that provides internet services, including personal and business access to the internet.
12. Internet Protocol (IP) Address
Internet Protocol (IP) Address- A numerical label that is assigned to devices participating in a computer network that uses the Internet Protocol for communication between its nodes.
Sunday, December 26, 2010
10. Hypertext Markup Language (HTML)
Hypertext Markup Language (HTML)- a set of tags and rules (conforming to SGML) for using them in developing hypertext documents.
6. File Transfer Protocol (FTP)
File Transfer Protocol (FTP)- a standard network protocol used to copy a file from one host to another over a TCP-based network, such as the internet.
4. Digital Certificate
Digital Certificate- an electronic document that verifies the owner of a public key, issued by a certificate authority.
3. Cookie
Cookie- A short line of text that a web site puts on your computer's hard drive when you access the web site.
1. ActiveX
ActiveX- An interactive technology used to run programs over the internet; for example, an ActiveX component can scan for viruses using a browser, instead of using an installed program.
Saturday, December 18, 2010
30. Worm
Worm- A software program capable of copying itself that can spread from one computer to the next over a network.
28. Urban Legend
Urban Legend- A story that appears mysteriously and spreads spontaneously in various forms and is usually not legit.
27. Trojan Horse
Trojan Horse- Non-self-replicating malware that appears to perform a wanted function for the user but instead facilitates unauthorized access to the user's computer system.
26. Time Bomb
Time Bomb- A computer program that has been written so that it will stop working after a predetermined date or time is reached.
24. Tagging
Tagging- A non-hierarchical keyword or term assigned to a piece of information such as an internet bookmark, digital image, or computer file.
22. RDF Summary
RDF Summary- A W3C specification that integrates a variety of applications, using XML as an inter exchange syntax.
21. Pyramid Schemes
Pyramid Schemes- the transfers of info or solicitation of persons through the Internet in an attempt to extort money or other valuables or the use of pyramid/chain letters are all illegal and all are prohibited.
20. Phishing
Phishing- The criminally fraudulent process of attempting to acquire sensitive information such as user names, passwords and credit card details by masquerading as a trustworthy entity in an electronic communication.
18. Logic Bomb
Logic Bomb- A piece of code intentionally inserted into a software system that will set off a malicious function when specified conditions are met.
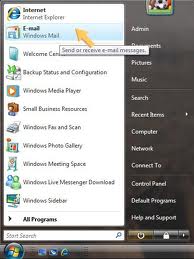
14. Windows Mail
Windows Mail- An e-mail and newsgroup client included in Windows Vista, that was superseded by Windows Live Mail.
13. User Agent
User Agent- A client application implementing a network protocol used in communications within a client-server distributed computing system.
12. Text Messaging
Text Messaging- The exchange of brief written messages between mobile phones over cellular networks.
11. Spam
Spam- A subset of spam that involves nearly identical messages sent to numerous recipients by e-mail.
Subscribe to:
Comments (Atom)